In 2025, phishing is larger and bolder, and it’s being more destructive with the help of AI. Cybercriminals are sending over 3.4 billion phishing emails a day, and over 1 million new phishing sites pop up every month. Phishing continues to be the first foothold of cybercriminals, and the average cost of a phishing-related data breach is a whopping $4.88 million.
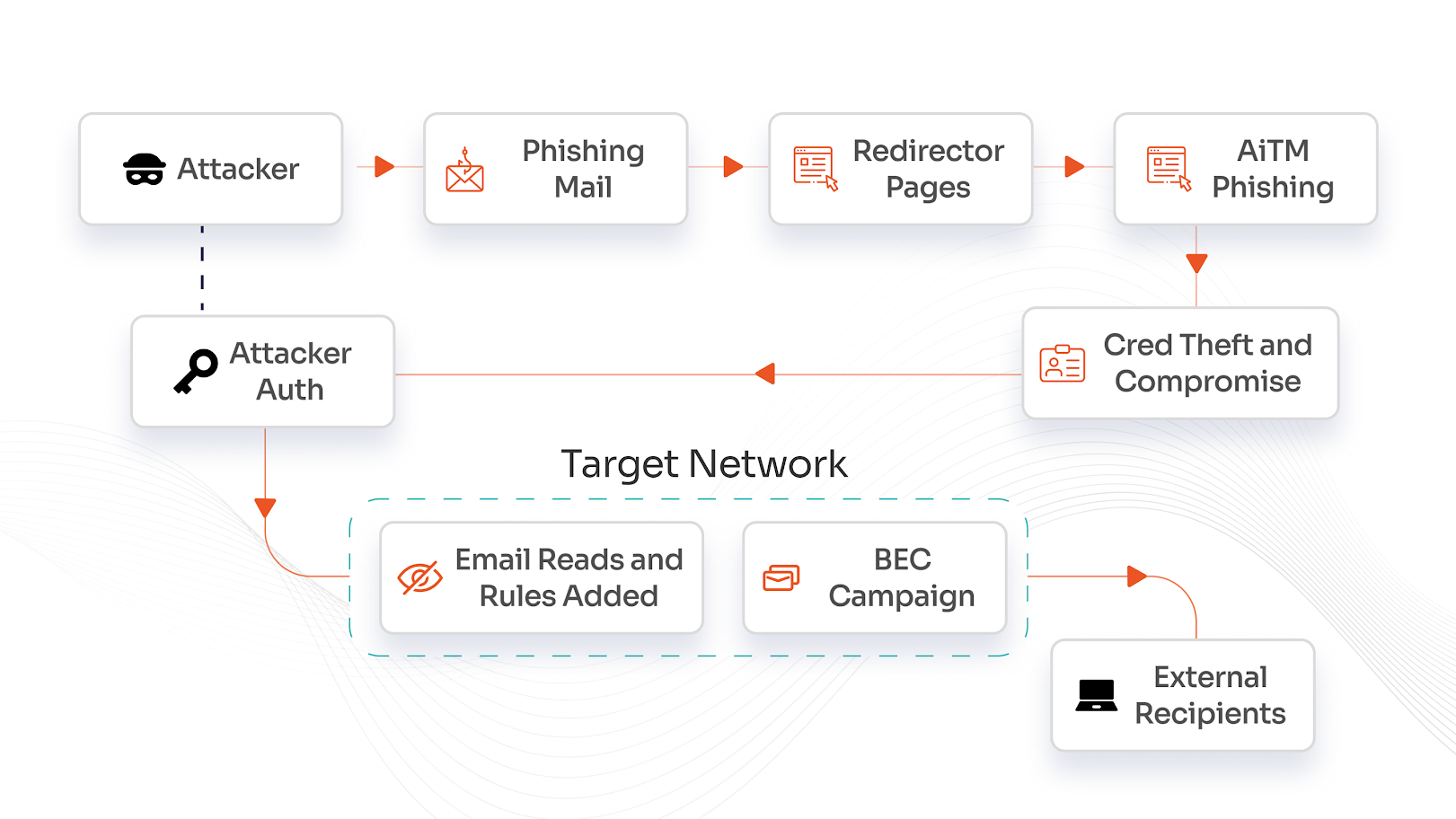
Imagine this: an email shows up in the inbox, it looks authentic and urgent. One click, submitting real credentials, and now the hacker is in. Once they are in, hackers can get past firewalls, create genuine-looking APIs, and even send users back to the real website to cover up their tracks. Smart, tireless, and always innovating, modern phishing does more than get your password; it takes over your full online identity in seconds.
Smart organizations are utilizing phishing-resistant MFA such as those created by miniOrange , because passwords are just the bait in today’s threat surface. Having secure access means sleeping at night, in the age of AI-based cybercrime.
What is Phishing-Resistant MFA?
Phishing-resistant MFA banishes the tactics that fail traditional authentication, like stolen passwords or phished one-time passcodes. It uses public or private key cryptography for identity proofing securely and never exposes reusable information. It is a passwordless MFA method.
So, why is this so practical?
- No shared secrets: You will share no passwords, no OTPs, and nothing for attackers to steal.
- FIDO2 + biometrics: Fingerprints and armored keys make impersonation next to impossible.
- User experience: Logins are faster, cleaner, and frustration-free since there are no codes to manage.
Phishing-resistant MFA leverages public key cryptography to authenticate users without relying on shared secrets like passwords or OTPs, eliminating the most common vector for phishing exploitation.
What is Phishing?
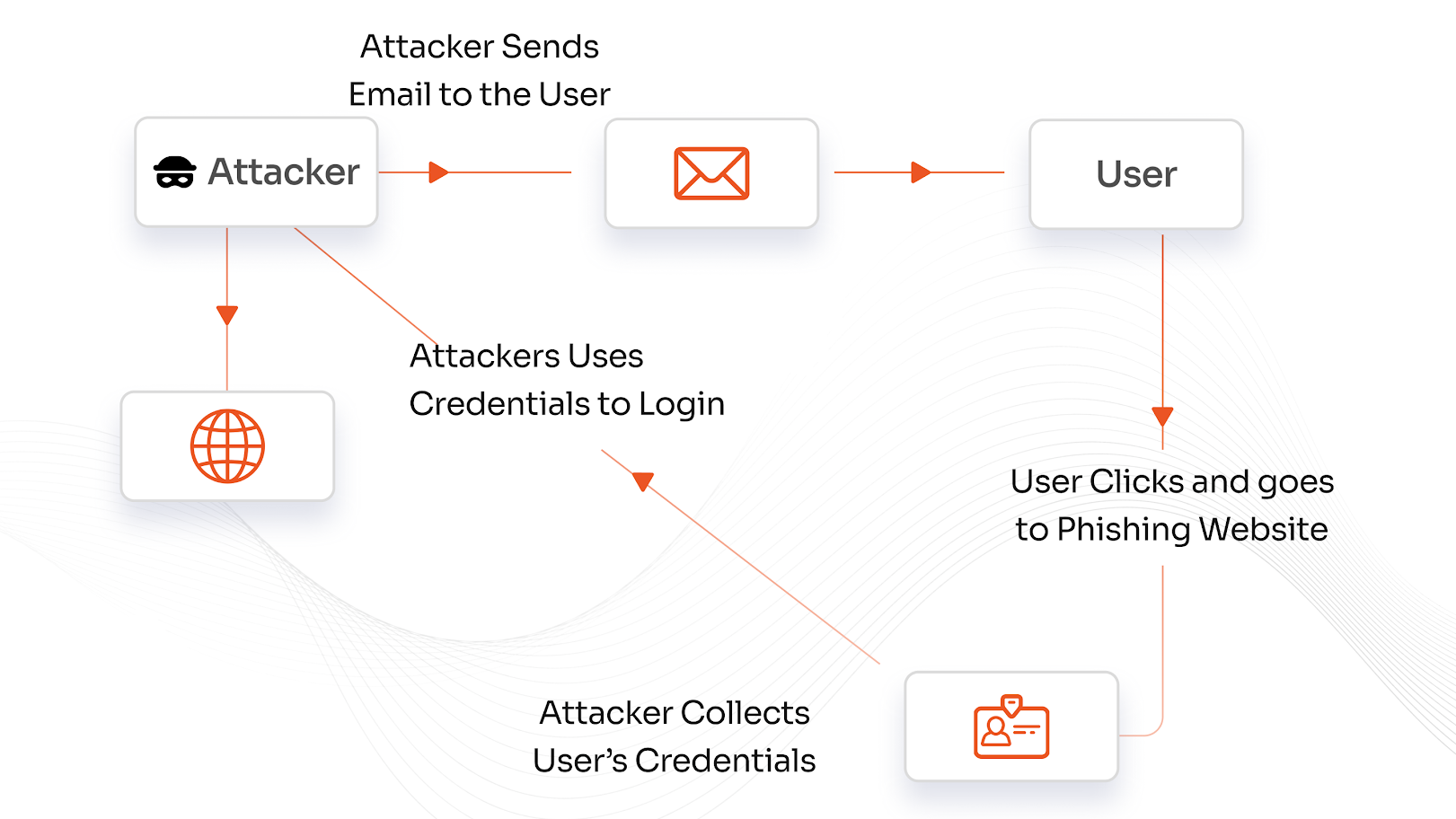
Phishing is a type of cyberattack in which the hacker tries to fool you into sharing private information (like a password or credit card number) by pretending to be a legitimate entity (like your bank or a familiar company). Scammers usually use email, messages, or fake sites to get you to share private information, which they then use for bad purposes.
What is Multi-Factor Authentication?
Multi-factor authentication (MFA) is a security procedure where the user attempts to access a system or application by providing two or more verification factors. Verification factors to confirm the user identity may include something you have (such as a smartphone or a hardware security token), something you are (such as fingerprint/face recognition), and something you know (such as a password).
Using more than one factor makes it double secure to gain access, as it then becomes sensitive to attackers or hackers attempting to gain authorization access to the application.
The Problem with Traditional MFA
Why not just use traditional MFA (if you have it)? It's akin to locking your front door and leaving the key under the mat.
- User Friction: Extra steps (like code entry) slow people down and make them frustrated. The result is that frustrated users take shortcuts and taking shortcuts compromises security.
- Phishing Vulnerability: Attackers can still fool SMS and email MFA through exploits like "push bombing." This results in human error being exploited by hackers, not weak technology.
- Shared Secrets are a Weakness: OTPs and passwords can be intercepted and reused in replay attacks. This results in if shared secrets can be copied, it is vulnerable to theft. And this is what attackers know very well.
Phishing-resistant MFA solves all of these by removing shared secrets altogether and providing organizations with a no-hassle secure solution.
Benefits of Phishing-resistant MFA
Organizations using phishing-resistant MFA realize several benefits outside of what’s typically associated with preventing phishing attempts:
- Cost Savings: Phishing attacks are expensive. Not just due to the direct monetary loss that occurs from the breach but also the downtime, reputational damage, and time spent to recover. A phishing-resistant MFA solution has the potential to reduce or eliminate these breach remediation costs for your organization.
- Easy Remote Access: Phishing-resistant MFA will allow access from anywhere safely and securely, this is especially beneficial for organizations that have a remote or hybrid workforce needing a scalable security solution as per the business size.
- Regulatory Compliance: Many industries have strict data security requirements to comply with and phishing-resistant MFA is the best way to meet the NIST 800-63-3, GDPR, and PCI DSS compliances, allowing access only by authenticated users to sensitive data.
- Polished User Experience: Because the focus of phishing-resistant MFA is designed to reduce extra steps that the customer takes, limiting the unproductive actions. This will improve productivity and satisfaction compared to normal MFA experiences and thereby raise the user adoption for the enterprise base.
In addition to reinforcing the security practices with phishing-resistant MFA, organizations can benefit from continued operational and financial savings. This is an investment into a security strategy that will ultimately deliver data protection, employee productivity, and customer care.
Types of Phishing-Resistant MFA
Stronger logins don’t have to mean clunky experiences. These MFA methods raise the bar for security while keeping things simple for users.
1. Biometric Authentication + Device Binding
Your face or fingerprint becomes the “key,” tied to your device. Even if hackers know your password, they can’t bypass your unique physical traits combined with a bound device. Secure, personal, and seamless biometric authentication along with device binding.
2. Push Notification Approval
Instead of typing codes, you get a quick approve/deny nudge on your trusted phone with a push notification. It’s instant, user-friendly, and far harder for attackers to hijack compared to SMS or email links.
3. Security Keys
A small hardware token you plug in or tap for verification, also known as token based authentication. Backed by FIDO2 standards, it renders phishing useless because login only works with your physical key in hand. Simple, portable, and nearly bulletproof.
4. Passkeys
Passwords without the headaches. Passkeys use device-based cryptography, syncing to your trusted devices. There’s nothing to remember, nothing to type, and nothing for attackers to steal.
5. One-Time Passwords via Authenticator Apps
Still better than SMS codes, app-generated OTPs refresh every few seconds and stay offline. While not the strongest option in this list, they add a valuable extra layer of security.
Stronger MFA doesn’t just stop attackers; it frees users from password fatigue. The future of authentication is clear: secure, smart, and stress-free.
Why is Phishing-Resistant MFA the Gold Standard?
Organizations are increasingly seeking resiliency against new and sophisticated phishing methods and are pursuing phishing-resistant MFA, which has gained traction among government agencies and top security standards organizations.
The U.S. Office of Management and Budget (OMB), in its Federal Zero Trust Strategy, identifies phishing-resistant MFA for their use because “credential theft remains one of the most common means adversaries use to gain access to sensitive information.” The U.S. government identifies it (OMB M-22-09) as the highest security standard for federal agencies to maximize accidental or intended phishing attempt reduction. It helps businesses comply with phishing-resistant MFA norms by the government.
The National Institute of Standards and Technology (NIST) advanced methods to achieve “verifier impersonation resistance,” the resistance to phishing.
- FIDO2/WebAuthn standardization makes phishing virtually impossible: companies like Microsoft and Google have observed decreases in account compromises by employees using security key hardware and realized the absence of breaches.
- Man-in-the-middle resistance: authenticates both the user and auth source, mitigates man-in-the-middle.
- Cloning/replay attacks prevention: eliminates credentials to be replicated or replayed.
- Require hardware-based secure computing elements: must utilize TPM/Secure Enclave or secure storage.
- Enhanced user experience with cryptography: users should always have what is required for signing with security.
- Better regulatory compliance: possible formalized documents for your organization to make statutory as well as GDPR, PCI DSS, and HIPAA.
Phishing-resistant MFA is the highest security level for federal agencies (OMB M-22-09). It provides real man-in-the-middle resistance by authenticating both the user and the authentication source, preventing cloning or replay attacks, requiring hardware-based solutions (e.g., TPM or secure enclave), enhancing user experience with biometrics, and naturally adjusting to help meet regulatory requirements (GDPR, PCI DSS, HIPAA).
miniOrange Phishing Resistant Multi-factor Authentication
The MFA offering phishing resistance does not just provide extra steps like those in traditional MFA. miniOrange phishing-resistant MFA offers passwordless, FIDO2/WebAuthn-certified security that is one of the most secure against phishing while being frictionless for the user.
- FIDO2/WebAuthn compliant: Login passwordless with the use of public key cryptography with a FIDO2/WebAuthn certified.
- Device-bound security: Your credentials are securely stored on your device, meaning nothing can be stolen.
- Biometrics: Authenticate using face, fingerprints, or hardware keys to provide excellent access without any friction.
- Proven 99.9% effective: If you compare phishing-resistant MFA and traditional MFA side-by-side, you will notice that phishing-resistant MFA is 99.9% more effective and reduces compromised accounts.
- Compatible with your identity systems: The miniOrange phishing-resistant MFA integrates seamlessly into your existing ecosystem. This tells us that you don’t have to destroy and rebuild your infrastructure.
- Omnichannel monitoring: Get alerts and detailed logs in real time to help you take control of your monitoring efforts.
- Compliant with known standards: Designed to meet the needs of GDPR, NIST 800-63-3, and PSD2.
No codes to enter, no secrets to steal, and no weaknesses to exploit. Just rock-solid security with a user experience that grows with your organization with miniOrange phishing-resistant adaptive MFA.
Getting Started with miniOrange Phishing Resistant MFA
83% of workers globally prefer hybrid arrangements with a mix of remote and office.
As your organization grows and transitions into a global remote or hybrid workforce, adding extra security features to your system helps you keep attackers at bay. With miniOrange’s phishing-resistant MFA, this transition becomes smooth. Our state-of-the-art security features with perfect coding and airtight MFA protection provides more than necessary security for any size of your organization. That means scalability is just a click away with seamless identity and access control at your fingertips.
Are you ready to move on to passwordless and phishing-free? Start your free trial of miniOrange phishing-resistant adaptive MFA to easily and securely authenticate or book a consultation with our experts.
FAQs
What is the difference between MFA and phishing-resistant MFA?
Multi-factor authentication adds extra layers of login security with passwords and codes and codes but can be phished. Phishing-resistant MFA works with FIDO2 security keys, hardware tokens, and biometrics that can’t be phished, or faked by hackers, like replacing a standard lock with a secret handshake that hackers can’t imitate.
What makes MFA “phishing-resistant”?
Phishing-resistant MFA does not use removable secrets, such as passwords or codes, but utilizes hardware tokens or biometrics with cryptographic confirmation. Only trusted devices can verify authentication, preventing phishing attempts and spoofing altogether.
How is passwordless MFA different from phishing-resistant MFA?
Passwordless MFA provides authentication that does not use passwords but biometrics or hardware tokens for instant and seamless logins. Phishing-resistant MFA produces cryptographic keys associated with your device, which deter phishing, just like a secret handshake combined with a bouncer who knows how to spot a fake ID.
Can phishing bypass 2FA?
Yes. Hackers utilize fake web pages, man-in-the-middle attacks, SIM card swaps, and social engineering to capture passwords and codes while logging. 2FA is of assistance, but is not infallible, however, phishing-resistant MFA provides greater protection.
Why are passkeys considered phishing-resistant?
Passkeys store encrypted keys on your own device that never leave it. This allows the site to be verified prior to its usage. If a false site is called, it is inaccessible because it has no access to the keys, which means that hackers cannot copy your login.
miniOrange
Author




Leave a Comment